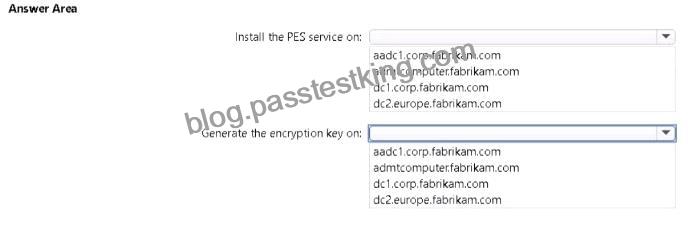
NO.83 You are planning the europe.fabrikam.com migration to support the on-premises migration plan-Where should you install the Password Export Server (PES) service, where should you generate the encryption key? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Topic 2, Contoso, Ltd
Existing Environment
Active Directory Environment
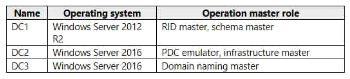
Contoso has an on-premises Active Directory Domain Services (AD DS) domain named contoso.com that syncs with an Azure Active Directory (Azure AD) tenant. The AD DS domain contains the domain controllers shown in the following table.
Contoso recently purchased an Azure subscription.
The functional level of the forest is Windows Server 2012 R2. The functional level of the domain is Windows Server 2012. The forest has the Active Directory Recycle Bin enabled.
The contoso.com domain contains the users shown in the following table.

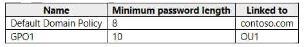
The contoso.com domain has the Group Policy Objects (GPOs) shown in the following table.
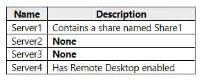
The contoso.com domain has the Password Settings Objects (PSOs) shown in the following table.

Server Infrastructure
The contoso.com domain contains servers that run Windows Server 2022 as shown in the following table.
By using Windows Firewall with Advanced Security, the servers have isolation connection security rules configured as shown in the following table.
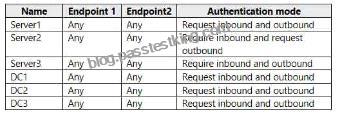
Server4 has no connection security rules.
Server4 Configurations
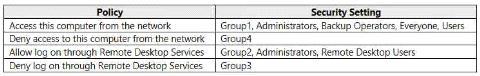
Server4 has the effective Group Policy settings for user rights as shown in the following table.
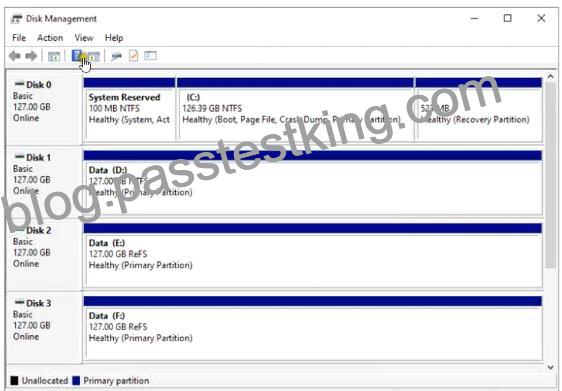
Server4 has the disk configurations shown in the following exhibit.
Virtualization Infrastructure
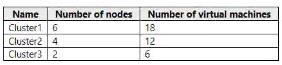
The contoso.com domain has the Hyper-V failover clusters shown in the following table.
Technical Requirements
Contoso identifies the following technical requirements:
Promote a new server named DC4 that runs to Windows Server 2022 to a domain controller.
Replicate the virtual machines from Cluster2 to an Azure Recovery Services vault.
Centrally manage performance alerts in Azure for all the domain controllers.
Ensure that User1 can recover objects from the Active Directory Recycle Bin.
Migrate Share1 to Server2, including all the share and folder permissions.
Back up Server4 and all data to an Azure Recovery Services vault.
Use Hyper-V Replica to protect the virtual machines in Cluster3.
Implement BitLocker Drive Encryption (BitLocker) on Server4.
Whenever possible, use the principle of least privilege.





